51% Attack Explained
Last Updated: 8th January 2019
A 51% attack refers to an individual miner, or group of miners controlling more than 50% of a network’s mining power, also known as hash rate or hash power. A network’s hash rate is a measure of the rate at which hashes are being computed on the network, a process that is known as hashing. Simply put, hashing involves taking an input string of a given length, and running it through a cryptographic hash function in order to produce an output of a fixed length. For example, hashing on the Bitcoin network requires the use of Secured Hashing Algorithm 256 (SHA-256), which is the cryptographic hash function that is used on the Bitcoin network. Numerous cryptocurrencies make use of differing hash functions, for example, Ethereum utilizes the ‘Ethash’ hashing function, whilst Litecoin’s cryptographic hash function is ‘Scrypt’. A network’s hash rate can usually be measured in the following denominations:
- 1 KH/s (kilohash per second) is 1,000 (one thousand) hashes per second
- 1 MH/s (megahash per second) is 1,000,000 (one million) hashes per second
- 1 TH/s (terahash per second) is 1,000,000,000,000 (one trillion) hashes per second
- 1 PH/s (petahash per second) is 1,000,000,000,000,000 (one quadrillion) hashes per second
Blockchains such as the Bitcoin blockchain are secured through a process known as proof-of-work (PoW). PoW involves individuals on the network, also known as miners, engaging in hashing in order to find the solution to a difficult mathematical problem. The more computational power a miner possesses, the higher the number of hashes that they will be able to compute, which means that they stand a better chance to find the solution to the problem before other miners on the network.
Miners that successfully solve the mathematical problem are given the right to add a block to the blockchain. In doing so, Miners secure the network by processing only valid transactions and ensuring that invalid transactions cannot be included in a block. Examples of an invalid transaction could be a wallet attempting to spend more money than it currently has or an individual engaging in double-spending. If a miner attempts to cheat, and includes an invalid transaction in a block, then the rest of the network will reject the block, and the miner would have wasted computational and financial resources performing PoW on that block. Miners that also accepted that block as valid and mined on top of what is actually an invalid block will also have wasted computational and financial resources.
Reversing Transactions and Double-Spends
However, an individual that controlled more than 50% of a network’s hash rate would be able to disrupt the network and render it insecure. With a 51% attack, the bad actor could reverse transactions and also engage in double-spending.
When a miner forms a valid block of transactions, the individual will normally broadcast the block to the rest of the miners on the network, so that other miners can verify its validity, which allows for consensus as to the shared state of the blockchain to be reached. However, a bad actor with more than 50% of a network’s hash rate could begin mining privately. They do this by mining from the same mempool, but transactions included in these privately mined blocks are not broadcasted to the rest of the network. This results in a scenario in which the public version of the blockchain is being followed by the rest of the network, but the bad actor is working on his own version of the blockchain and not broadcasting it to the rest of the network.
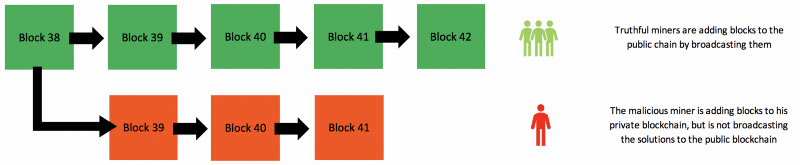
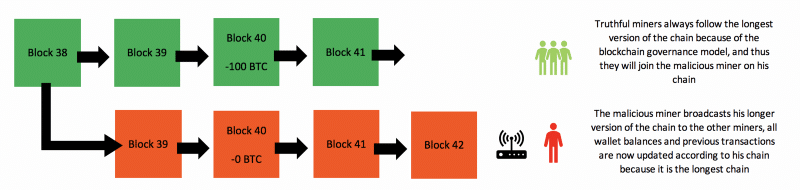
With this in mind, the bad actor can now engage in double-spending. They can do this by first spending their bitcoins on the public version of the blockchain, but then not include these transactions on the blockchain that has not been broadcasted. On this private version of the blockchain, the bad actor still possesses those spent bitcoins. Because the bad actor is in control of a considerable amount of hashing power (more than 50%) they will be able to broadcast their private version of the blockchain and form blocks faster than the rest of the network, which means that they will be able to form a longer blockchain. Because of the longest chain rule, it is generally regarded that the longest blockchain is the valid chain to mine upon. As a result, the rest of the miners on the network will be forced to switch to the longer chain. The previously private version of the blockchain is now considered to be the correct one, and all transactions that were not included on this chain are reversed. The bad actor also retains his bitcoins as he did not include those spent transactions on this version of the blockchain, meaning that those funds are capable of being spent again.
Source: Coinmonks
In practice, carrying out a 51% attack is extremely difficult, as the bad actor would need more hashing power than the rest of the entire network combined. Achieving such a feat would require a significant financial commitment that is usually sufficient to deter individuals from trying. However, this is dependent on a network’s hash rate, as the financial barrier to carrying out a 51% attack may be lower on a network with a low hash rate. Moreover, the chances of successfully carrying out a 51% attack may be more likely if one acknowledges the existence of mining pools, which effectively allow miners to combine their computational power on any given network.





[…] secure because its large node count makes sybil attacks difficult, and its high hash rate makes 51% attacks expensive. However, the remaining property it fails in is […]
[…] secure because its large node count makes sybil attacks difficult, and its high hash rate makes 51% attacks expensive. However, the remaining property it fails in is […]
Comments are closed.