What Is SHA-256 And How Is It Related to Bitcoin?
Last Updated: 24th April 2022
SHA-256 is a cryptographic hash function within the SHA-2 (Secure Hash Algorithm 2) family of hash functions. It was developed by the NSA in 2016 following the breakdown of it's predecessor SHA-1. SHA-256 has never been compromised and is considered one of the most secure cryptographic hash functions. As a result, it's one of the most popular cryptographic hash functions in the cryptocurrency world. This article will cover how SHA-256 works and how it's used within Bitcoin specifically.
The SHA-256 hash function takes an input of a random size and produces an output of a fixed size. Hash functions are powerful because they are ‘one-way’. What this means is that it's possible for anyone to use a hash function to produce an output when given an input; however, it is impossible to use the output of the hash function to reconstruct its given input. This powerful feature of the SHA-256 hash function makes it ideal for application within the Bitcoin network.
The SHA-256 hash function is utilised within the Bitcoin network in two main ways:
- Mining
- Creation of Bitcoin addresses
Mining
Mining is a process by which new coins are introduced into the existing circulating supply of the Bitcoin protocol, as well as a method used to secure the Bitcoin network.
For an individual to be eligible to add a block to the Bitcoin blockchain, they must first operate what is known as a mining node. Upon successfully setting up a mining node, an individual can then begin constructing candidate blocks which are then relayed to the Bitcoin network in order to be checked for their validity. Inside a block is what is known as a block header; to construct a block there are 6 parameters that must be filled in by the miner. These include:
- Version – Version number of the Bitcoin software
- Previous block hash – Reference to the hash of the previous block
- Merkle Root – A representative hash of all transactions included in the block
- Timestamp – The time at which the block was created
- Target – Proof-of-work algorithm for the block
- Nonce – The variable used in the proof-of-work process
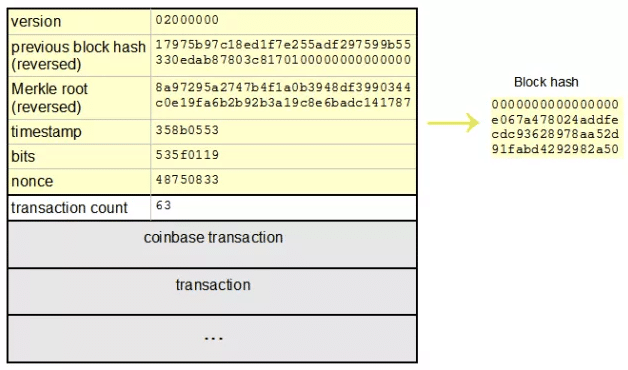
As can been seen from the image above, in order for a miner to produce the previous block hash parameter, the block header of the previous block must be put through the SHA-256 algorithm twice, this also known as double-SHA-256. That is:
Previous Block Hash = SHA-256(SHA-256(Block Header))
The SHA-256 algorithm is also used to produce the merkle root, which is then subsequently inserted into the block header. A comprehensive explanation of this aspect of the Bitcoin protocol can be found here: Merkle Tree & Merkle Root Explained.
Upon successful construction of a block, the miner can now begin the mining process, wherein another use case of the SHA-256 algorithm will present itself. In this instance, one parameter of the block header, the nonce, is a variable that is changed repeatedly, and upon hashing of the block header using the SHA-256 function, if the hash is below the target, the miner is considered to be successful.
For example, if the nonce were to have a variable “12345”, this would be placed in the block header alongside the other 5 parameters listed above. The block header would then be hashed, however, if the resulting hash proves to be above the target, the miner must try again. The miner can then change the nonce to another variable, e.g. “90872”, and place this inside the block header, with the other 5 parameters remaining constant. The resulting hash proves to be below the target, thus, the miner's block is then relayed to the network to ensure that it is valid.
Creation of Bitcoin addresses
In order to produce a Bitcoin address, a private key, which is a randomly selected number, is multiplied using an elliptic curve to produce a public key. This public key is then put through both the SHA-256 and RIPEMD160 hashing algorithms.
Where K = the public key and A = Bitcoin address:
A = RIPEMD160(SHA-256(K))
The use of the SHA-256 and RIPEMD160 hashing algorithms for the creation of a Bitcoin address has one distinct advantage:
- Shorter addresses
Shorter addresses: A public key is 256 bits long whereas, the hashed version, i.e the Bitcoin address, is 160 bits long. This makes it a lot more convenient for users to use due to the shorter character length.
Conclusion
To conclude, the SHA-256 hashing algorithm is an integral part of the Bitcoin protocol. It has seen implementation in varying facets of the technology such as: bitcoin mining, merkle trees, and the creation of Bitcoin addresses.





[…] on the Bitcoin network requires the use of Secured Hashing Algorithm 256 (SHA-256), which is the cryptographic hash function that is used on the Bitcoin network. Numerous […]
[…] on the Bitcoin network requires the use of Secured Hashing Algorithm 256 (SHA-256), which is the cryptographic hash function that is used on the Bitcoin network. Numerous […]
Comments are closed.